Currently exist a lot of methods to perform a de-authentication attack in a wireless environment. As a part of my previous post, I will go into deep detail about the easiest way to perform an attack in your own wireless lab. For this example I will perform this attack with the next parameters in my lab:
Evil Machine
VM1: Kali Linux
Wireless adapter: AWUS036ACH
Victim
VM2: Ubuntu 20.04.3
Wireless adapter: TP-Link 802.11ac
For the purposes of this lab, I preferred to work with Ruckus just for flexibility in configuration but if you prefer to reproduce this lab in another brand is totally possible:
Controller Version 6.0.0.0.1331
Control Plane Software Version 6.0.0.0.1213
AP Firmware Version 6.0.0.0.1594
SSID: RuckusLab
Band: 2.4GHz
Channel: 1
Authentication options: Standard Open
Encryption: WPA2 Algorithm AES
As I told previously the easiest way to perform a de-authentication attack is with three simple tools available airmon-ng, airodump-ng, and airplay-ng
- The first step is to put your wireless interface in monitor mode

- After that, you need to check the BSSID in the air and the stations connected
#airodump-ng wlan0
- Knowing the BSSID target and the channel where is operating we need to define the correct parameter to set the airodump-ng on the correct channel and start to send messages to the BSSID
- Now you are ready to launch a de-authentication attack, setting the params of -a BSSID and -c STA mac address
- I love this Ruckus function of OTA(On the Air) capture because allow me to have a sample of what is happening with my users, now my SSID is only radiated on 2.4GHz and that is the reason to use that band and I'm filtering by client MAC to reduce the size of the sample
Sending CTRL+C, I stopped the de-authentication attack
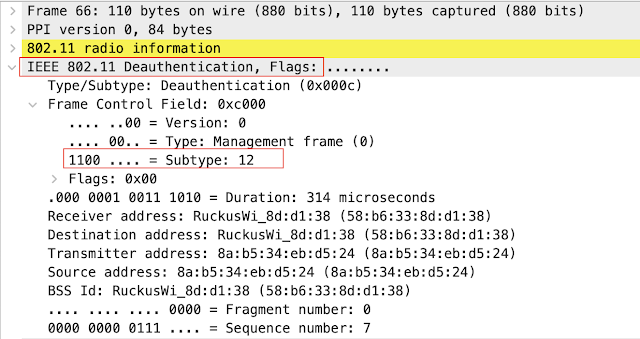
- Now I can take a look of what is happening in the controller side filtering with:
(wlan.fc.type == 0) && (wlan.fc.type_subtype == 0x0c)
OR
(wlan.fc.type eq 0) && (wlan.fc.type_subtype eq 0x0c)
OR
(wlan.fc.type eq 0) && (wlan.fc.type_subtype eq 12)
- It is a pretty similar view from the attacker's side
As I show you this is a very simple process to perform a de-authentication attack with just basic wireless hardware and a few software tools available for anyone on the Internet. My next post is about the options in Ruckus SmartZone to mitigate these kinds of attacks and how we can activate and the results of this process
%3CmxGraphModel%3E%3Croot%3E%3CmxCell%20id%3D%220%22%2F%3E%3CmxCell%20id%3D%221%22%20parent%3D%220%22%2F%3E%3CmxCell%20id%3D%222%22%20value%3D%22%22%20style%3D%22points%3D%5B%5B0.005%2C0.09%2C0%5D%2C%5B0.08%2C0%2C0%5D%2C%5B0.76%2C0.25%2C0%5D%2C%5B1%2C0.92%2C0%5D%2C%5B0.91%2C0.995%2C0%5D%2C%5B0.57%2C0.995%2C0%5D%2C%5B0.045%2C0.955%2C0%5D%2C%5B0.005%2C0.43%2C0%5D%5D%3BverticalLabelPosition%3Dbottom%3Bsketch%3D0%3Bhtml%3D1%3BverticalAlign%3Dtop%3Baspect%3Dfixed%3Balign%3Dcenter%3BpointerEvents%3D1%3Bshape%3Dmxgraph.cisco19.3g_4g_indicator%3BfillColor%3D%23005073%3BstrokeColor%3Dnone%3Bdirection%3Dsouth%3Brotation%3D120%3B%22%20vertex%3D%221%22%20parent%3D%221%22%3E%3CmxGeometry%20x%3D%22785%22%20y%3D%22440%22%20width%3D%2225%22%20height%3D%2225%22%20as%3D%22geometry%22%2F%3E%3C%2FmxCell%3E%3C%2Froot%3E%3C%2FmxGraphModel%3E











No comments:
Post a Comment