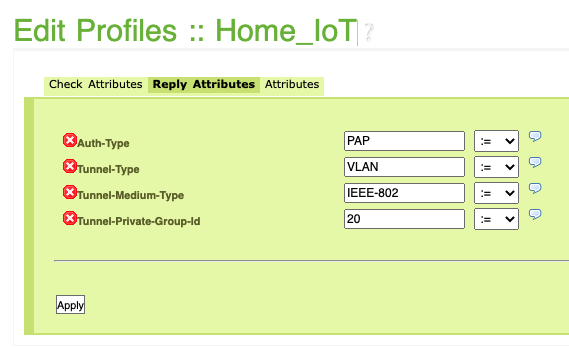
Find and modify the following lines according to your environment
server = "localhost"
port = 3306
login = "radius"
password = "Password1234!"
radius_db = "radius"
radius_db = "radius"
read_clients = yes
client_table = "nas"
Modify the permission of the mods-available files and reload the Freeradius service
sudo chgrp -h freerad /etc/freeradius/3.0/mods-available/sql && sudo chown -R freerad:freerad /etc/freeradius/3.0/mods-enabled/sql
sudo systemctl restart freeradius.service
Three files must be modified to allow the correct operation in the radius server:
/etc/freeradius/3.0/radiusd.conf
/etc/freeradius/3.0/sites-available/default
/etc/freeradius/3.0/mods-available/sql
Go to the radiusd.conf find the lines and modified the next parameters:
auth = yes
auth_badpass = yes
auth_goodpass = yes
Go to the /etc/freeradius/3.0/sites-available/default find the lines and modified the next parameters:
Authorization Queries
Go to the /etc/freeradius/3.0/mods-available/sql find the lines and modified the next parameters:
driver = rlm_sql_mysql
dialect = "mysql"
Connection info uncomment
password = "Password1234!"
read_clients = yes
DROP TABLE radacct;
CREATE TABLE radacct (
radacctid bigint(21) NOT NULL auto_increment,
acctsessionid varchar(64) NOT NULL default '',
acctuniqueid varchar(32) NOT NULL default '',
username varchar(64) NOT NULL default '',
groupname varchar(64) NOT NULL default '',
realm varchar(64) default '',
nasipaddress varchar(15) NOT NULL default '',
nasportid varchar(32) default NULL,
nasporttype varchar(32) default NULL,
acctstarttime datetime NULL default NULL,
acctupdatetime datetime NULL default NULL,
acctstoptime datetime NULL default NULL,
acctinterval int(12) default NULL,
acctsessiontime int(12) unsigned default NULL,
acctauthentic varchar(32) default NULL,
connectinfo_start varchar(50) default NULL,
connectinfo_stop varchar(50) default NULL,
acctinputoctets bigint(20) default NULL,
acctoutputoctets bigint(20) default NULL,
calledstationid varchar(50) NOT NULL default '',
callingstationid varchar(50) NOT NULL default '',
acctterminatecause varchar(32) NOT NULL default '',
servicetype varchar(32) default NULL,
framedprotocol varchar(32) default NULL,
framedipaddress varchar(15) NOT NULL default '',
framedipv6address varchar(45) NOT NULL default '',
framedipv6prefix varchar(45) NOT NULL default '',
framedinterfaceid varchar(44) NOT NULL default '',
delegatedipv6prefix varchar(45) NOT NULL default '',
class varchar(64) default NULL,
PRIMARY KEY (radacctid),
UNIQUE KEY acctuniqueid (acctuniqueid),
KEY username (username),
KEY framedipaddress (framedipaddress),
KEY framedipv6address (framedipv6address),
KEY framedipv6prefix (framedipv6prefix),
KEY framedinterfaceid (framedinterfaceid),
KEY delegatedipv6prefix (delegatedipv6prefix),
KEY acctsessionid (acctsessionid),
KEY acctsessiontime (acctsessiontime),
KEY acctstarttime (acctstarttime),
KEY acctinterval (acctinterval),
KEY acctstoptime (acctstoptime),
KEY nasipaddress (nasipaddress),
INDEX bulk_close (acctstoptime, nasipaddress, acctstarttime)
) ENGINE = INNODB;
exit;